Now you're all probably asking "How do I convert my list into base64 keys?" Well it's very easy and I will explain.
First you will need a ftp domain. I use a free one like 000webhost
Next you will need a little word list conversion tool. You will need one because with Base64 the user and pass are together like so >> username:password << I use List Master by Markus a old friend of mine or S-WordTool which was coded by Beda. I prefer to use List Master, you can get it from me here > List Master < so you would want to load your password list into the program than use the 'Add string in front of all' that's where you would add your username like admin.
Here's a picture for an example...
After saving your list we need to encode it to Base64...
<?php
$passes = file('swing.txt');
foreach($passes as $key => $pass)
$passes[$key] = base64_encode($pass);
$passes = implode("\n", $passes);
file_put_contents(doggy, $passes);
?>
With this php code we can encode the User:Pass to Base64
Copy and paste the php code in a text and save it as a php file.
Next you're going to want to upload the php file to your ftp, mine is titled base64_encode.php
After, upload your conversion list. 'User:Pass' mine is titled swing.txt in the php code.
After you have uploaded the 2 files to your ftp make sure to give the files full permissions...
After this is all done visit your page 'http://website.com/base64_encode.php'
Once you go to the url of your php you will see nothing but white background.
Now you will want to go to 'http://website.com/doggy'
You should see all your 'User:Pass' from your conversion list are now in Base64 format on the doggy page.
Save this as a text list on your computer 'file.txt'
Note* If you ever get blank lines in-between each Base64 key just use List Master and load your list and the blank lines will be removed than re-save your text list.
You are also wondering well if I load a big Base64 list and I hit one how am I suppose to know what it is in plain text to login. Well that's very easy there's two ways to do it.
The first way is we can decode the Base64 back to plain text by using this php code...
<?php
$passes = file('swing.txt');
foreach($passes as $key => $pass)
$passes[$key] = base64_decode($pass);
$passes = implode("\n", $passes);
file_put_contents(doggy, $passes);
?>
It will decode a Base64 key back to 'User:Pass' in plain text rather than encode it.
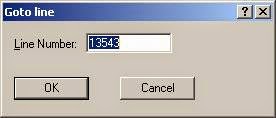
The second way is to open your Base64 *.txt and find your Base64 key you cracked. So you would click edit, find in your *.txt and put in the Base64 key, lets say it's YWRtaW46YWRtaW4= which is admin:admin in plain text. Once you have found the Base64 Key in your *.txt click edit, go to
My Base64 key YWRtaW46YWRtaW4= is on line 13543
Now you would want open your conversion list *.txt 'User:Pass' and click edit, go to and type in the line number you see your Base64 key is on.
As you can see the cursor is on admin:admin so that's the second method. Not to hard really.
So now that we know how to convert a Base64 key back to plain text we need to talk about debugging a program. No program is perfect there's always some sort of bug. I try my best to run test, lots of test for accuracy. The goal is to have your program be 100% accurate, so we need to run debug tests for this reason.
There's 1 bug in my brute force cracker I have to share. It deals only with v1 not v2 so if you're using v2 you don't have to worry about this bug. For v1 however there is a bug and to explain it, I will show you the tests I ran to find it and pin point on what needs to be done for 100% accuracy. I'm not about to try and fix the bug because it's much easier to do this than rewrite my array.
So I tested my v1 brute force cracker by using a base64 string to a host that I knew the pass to. Well it didn't hit the host on the first line or the second line but on the third line it worked. So in other words the first 2 lines on your base64 list should be junk data it will not hit the correct password on the first 2 lines. So don't be loading or adding good base64 keys to the first 2 lines of your list.
Here some examples to prove this...
Before:
After:
No Hit on this test. The first two lines have the correct base64 key and the last line is junk data. It did not hit the host on the first 2 lines.
Before:
After:
No hit on this test. The correct Base64 key is on the 2nd line as you can see.
Now let's test the Base64 key on the 3rd line.
Before:
After:
It cracked the host as you can see, on the 3rd line.
Your list should look like this before loading it or adding your Base64 keys manually...
junk <------------ 1st line is junk data
junk <------------ 2nd line is junk data
YWRtaW46MTIzCg== <------------ 3rd line is the starting point
YWRtaW46MTIzNAo=
YWRtaW46MTIzNDUK
YWRtaW46MTIzNDU2Cg==
YWRtaW46MTIzNDU2Nwo=
YWRtaW46MTIzNDU2NzgK
YWRtaW46MTIzNDU2Nzg5Cg==
YWRtaW46MTIzNDU2Nzg5MAo=
YWRtaW46NDMyMQo=
YWRtaW46NTQzMjEK
YWRtaW46NjU0MzIxCg==
YWRtaW46NzY1NDMyMQo=
YWRtaW46ODc2NTQzMjEK
YWRtaW46OTg3NjU0MzIxCg==
YWRtaW46MDk4NzY1NDMyMQo=
YWRtaW46MTExCg==
To show that the 4th line works after the 3rd we will do the final test...
Before:
After:
Now that we know how to setup the cracker for 100% accuracy we're good to go.
Okay lets go through the specs of the cracker.
-It was written in Visual Basics, so make sure to download the run-time files needed.
-Developed for Windows.
-You can upload any amount of Base64 strings, there's no limit.
-Available port control, so you can change the port if needed.
-String customization available, you can change the string to what you need. Like GET or POST
-Host control for who you're going after.
-Return code available, this allows you to pick a return on what you want back on a crack.
-No multi socket support, we don't want to lag or ddos our host. v2 has socket control.
One thing and I will make crystal clear. Make sure your host only has Basic Authorization within the packet, nothing else. The cracker will not work right if you don't make sure it's only a Basic Authorization.
You want your packet when you analyze it to look like this...
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Basic realm="Linksys EA2700"
Content-Type: text/html
Content-Length: 351
Date: Mon, 08 Dec 2014 04:34:06 GMT
Server: lighttpd/1.4.28
The part you want to look for is this...
WWW-Authenticate: Basic realm=
Now if you see this and more Authenticates my cracker will not work with those.
So only try to crack host that contain WWW-Authenticate: Basic realm= and only that.
It's always a good idea to keep a routine to check on your packet analyzer on how you're doing while you're cracking.
You can find them online for free everywhere.
My cracker is not for noobs or people that don't understand base64 or anything of the matter. This is made for people with the knowledge of understanding returns, strings, and such. I'm not going to go through everything for people so if you don't understand it, learn.
I'm making a router/modem scanner. The scanner will go hand in hand with v2. It will be released at a later date.
I will show a example of v2 on how to load your hosts.
So make sure when loading your list, to load it with the :port with the host. This is because when list cracking you might find hosts on different ports and you will want to crack them on that port. So this is the best way to go about it. Plus my router/modem scanner when finding hosts will have the :port included, making cracking much easier with the brute force base64 list cracker.
In the download I will include both versions of the brute force base64 cracker. Both the encode and decode of Base64 in php file format.
You can grab it here > PR Base64 Brute
Happy hunting...
People that follow my blog have been asking for a port scanner that scans 1 host against ports. Well I thought I should make one so I did for you all.
It's pretty easy to use. It's not exactly fast because we want it to be 100% accurate and know that it's reliable.
- You can add your ports manually if you wish. Load a list of ports if needed. You can also port gen a list if you want to scan a host against a gen of ports. The generator generates the ports 1 to 20000 and it very handy to use.
- No socket or timeout control available. Like I said we want it to be 100% accurate and it's. The only way it would miss a hosts open port is if it's behind a firewall or lagging incredibly bad.
v2 is the list version. It's like my other port scanner which I released but this one has a IP Gen option now. The IP Gen, generates a ip range from 0.0 to 255.255. So in other words, if your ip was 76.45.3.126 and you wanted to scan the whole ip range within that ip. You would type in 76.45 and click IP Gen. That would generate the ips from 76.45.0.0 to 76.45.255.255. This makes list port scanning much easier for you guys.
You can grab v1 and v2 here... PR TCP Port Scanner v1-v2
Well I was bored for the last few days, so I made a DDOS program for fun.
So this program is for ddosing stuff like routers, modems, cams, printers, etc...
I originally made it for ddosing comcast routers.
You could ddos lots of other stuff the way I made it.
How you use it.....
-First you would want to open my program at least 7 to 8 times. So you should have 7 to 8 instances of my program open For most hosts it takes that much. For some it might take as little as 4 or as little as 1. Test the host yourself.
-Second you put the host you're targeting in the text box under Host Gen, and then click Host Gen for all instances of my program open.
-Third you open my text I provided called DDOS-Data.txt and copy all the data from with in it. Then paste it in to the text box called DDOS Data: in all instances of my program being open. You will see that it looks like it didn’t paste into the text box but trust me it's in there.
I have to also tell you all, that some host reject the large amount of data and accept as little as a 'hi'. I was running 1 instance of my program trying a host running an abus cam and it would reject the large data dump but accept a 'hi'. It gave me a '503 Service Temporarily Overloaded' response when I would visit the page. So play around with the program there’s lots of ways to trick a server.
-Fourth you need to have a packet analyzer to analyze the host you want to attack. To write the string and user:pass. Remember it only works off of POST and a login. You want to make sure you test the host without the DDOS-Data.txt first and just add some random word with 1 instance. You are looking for a 200 OK response back or better to take the host down. This does not mean a 400 Bad Request won't get ddos, it all depends on what size of data they have to send back.
-Fifth you will need to hit start on all instances of my program open.
This will run large amounts of data to the target. It may not time-out the host but it will definitely lag them really bad.
You will need a good connection and large amounts of virtual memory to pull this attack off.
The way the program works is that it sends large amounts of data to the target and sends an illegal request.
It will not work on every host. We want to attack hosts that have weak security to begin with.
This is called lame for a reason because it's lame but it works.
Make sure to test the host while you're attacking them with a different ip address. If you're attacking them from home you could use tor I suppose to test the host.
Host I took down using this program:
Abus Cam - Unknown Version - Took Down - 503 Service Temporarily Overloaded - 1 Instance - 'hi' Used - DDOS-Data.txt Rejected
BL-C20 Version 1.32 - Took Down - Connection Reset - 1 Instance - DDOS-Data.txt Used
Vigor 2920n - Took Down - Unable to connect - 1 Instance - DDOS-Data.txt Used
Heatmiser WiFi thermostat - Took Down - The connection has timed out - 1 Instance - DDOS-Data.txt Used
I stopped after this point.
I'm not responsible if your isp shuts you down or you end up in jail. This is no joke; make sure you know what you're doing and always use this sort of tool as that, not a toy. Don't let the title of the program fool you this does work and you don't want a knock at your door.
Lucky it's the New Year or I wouldn't give this out for free.
You can grab it here... PR Lame DDOS v1
PR Digital Watchdog VMAX Web Viewer Vulnerability Scanner
As the name goes, it goes hand in hand with Vulnerability it grabs only Digital Watchdog VMAX Web Viewer though. Every host you find you can view them with admin no password. Have fun with this one because Digital Watchdogs sure messed up.
You can get it here... PR VMAX Web Viewer Vulnerability Scanner















No comments:
Post a Comment